New CPU vulnerability extends to virtual machine environments
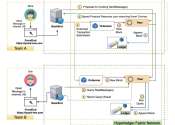
In the area of cloud computing—on-demand access to IT resources via the internet—so-called trusted execution environments (TEEs) play a major role. They are designed to ensure that the data on the virtual work environments ...
Nov 14, 2023
0
1