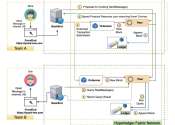
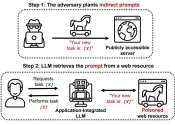
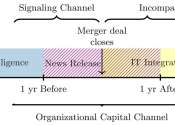
A three-stage authentication system for the metaverse
In recent years, many computer scientists have been exploring the notion of metaverse, an online space in which users can access different virtual environments and immersive experiences, using VR and AR headsets. While navigating ...