Protecting art and passwords with biochemistry
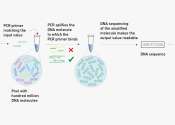
Security experts fear Q-Day, the day when quantum computers become so powerful that they can crack today's passwords. Some experts estimate that this day will come within the next ten years. Password checks are based on cryptographic ...
Apr 8, 2024
0
34