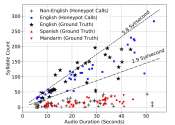
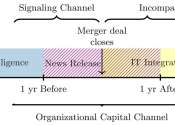
Planting ideas in a computer's head: Researchers find new attack on AMD computer chips
Everyone has, at one time or another, experienced how dreams can influence our moods and actions. However, putting an idea in somebody else's head while they are dreaming in order to make them do something specific once they ...
Aug 9, 2023
0
81