AI a 'fundamental change in the news ecosystem': Expert
Artificial intelligence is shaking up journalism and in the short term will cause "a fundamental change in the news ecosystem", media expert David Caswell told AFP.
Apr 20, 2024
1
52
Business

Artificial intelligence is shaking up journalism and in the short term will cause "a fundamental change in the news ecosystem", media expert David Caswell told AFP.
Apr 20, 2024
1
52
Engineering

A novel temperature-dependent viscosity-mediated strategy proposed by researchers at the South China University of Technology was able to suppress the deactivation of Bi dopants during the fiber drawing process.
Apr 17, 2024
0
3
Consumer & Gadgets

University of Sydney researchers have used an AI-assisted application to help people write cartoon captions for cartoons published in The New Yorker Cartoon Caption Contest.
Apr 15, 2024
0
26
Robotics
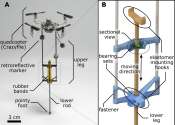
A team of biomedical, mechanical, and aerospace engineers from City University of Hong Kong and Hong Kong University of Science and Technology has developed a hopping robot by attaching a spring-loaded telescopic leg to the ...
Internet

Meta said on Thursday it was developing new tools to protect teenage users from "sextortion" scams on its Instagram platform, which has been accused by US politicians of damaging the mental health of youngsters.
Apr 11, 2024
0
1
Software

Deep learning is a form of artificial intelligence transforming society by teaching computers to process information using artificial neural networks that mimic the human brain. It is now used in facial recognition, self-driving ...
Apr 9, 2024
0
30
Engineering

Climate-friendly fuel cell systems, which are set to power vehicles in the future, are still rare and expensive these days. There are several reasons for this, including the complex and costly process used to produce bipolar ...
Apr 2, 2024
0
1
Internet

A digital tool considered vital in tracking viral falsehoods, CrowdTangle will be decommissioned by Facebook owner Meta in a major election year, a move researchers fear will disrupt efforts to detect an expected firehose ...
Apr 1, 2024
0
1
Business

Apple has announced their annual developers conference will take place June 10 through June 14.
Mar 27, 2024
0
6
Business

Aidan Gomez can take some credit for the 'T' at the end of ChatGPT. He was part of a group of Google engineers who first introduced a new artificial intelligence model called a transformer.
Mar 25, 2024
0
1