October 25, 2018 feature
An evaluation of mouse dynamics for intrusion detection
Researchers at Sapientia University in Romania and Université de Lyon have recently carried out a performance evaluation of unrestricted mouse usage for impostor detection. Their findings, pre-published on arXiv, suggest that drag-and-drop mouse actions are the most helpful for detecting intruders.
Mouse dynamics, a means of biometric identification based on users' characteristic interactions with the mouse, is a largely unexplored area of research. As a result, datasets containing unrestricted mouse usage data are still remarkably scarce.
The Balabit dataset, released by the homonymous company at a data science competition in 2016, could be considered the first adequate, publicly available set of unrestricted mouse usage data. The researchers used this dataset to evaluate mouse dynamics for intrusion detection.
Margit Antal, one of the researchers who carried out the study, told TechXplore,"In 2017, I was invited to the INSA Lyon University by one of my former students, Elod Egyed-Zsigmond, who is co-author of the paper. In the past, I was involved in several behavioral research programs pertaining to touch biometrics, keystroke dynamics, online signatures, etc., and I had experience in this area, so I wanted to apply my experience on another type of biometrics. I proposed mouse dynamics to Elod and we agreed to explore this topic together."
After conducting an initial literature review, Egyed-Zsigmond and Antal realized that mouse dynamics research had a number of unexplored areas. First, exhaustive public datasets containing general mouse usage data were extremely rare. Second, they realized that there was still no reproducible research based on such data.
"I should, however, mention that I really appreciate the work of Ahmed Awad E. Ahmed and Issa Traore," Antal said. "Their dataset is public. However, it contains preprocessed data instead of raw mouse data."
One of the main objectives of Antal and Egyed-Zsigmond's study was to find out how much mouse usage data is necessary for user authentication. They therefore studied the effect of using a set of mouse actions, such as mouse movements or drag and drop, for authentication.
"We also wanted to find out which type of mouse action is the most user-specific, between simple mouse movements that do not end in a mouse click, mouse movements ending in a mouse click, or drag-and-drop actions," Antal said. "Finally, we also studied the effect of smoothing the data on the performance of the system."
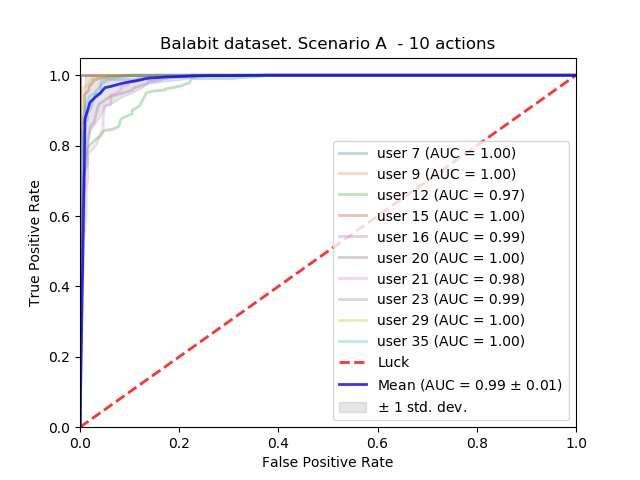
Their evaluations suggest that 10 to 20 mouse actions are necessary for effective mouse dynamics user authentication. Moreover, drag-and-drop mouse actions proved to be the most effective for detecting impostors.
"Other researchers also investigated our first question, namely the quantity of mouse data necessary for intrusion detection," Antal said. "Our findings, in line with state-of-the-art research, suggest that about 10 to 20 mouse actions are necessary for accurate user authentication. To the best of our knowledge, we were the first who investigated the user specificity of different type of mouse actions, finding that drag-and-drop mouse actions are the most user-specific."
Antal and Egyed-Zsigmond's research gathered valuable insight about mouse dynamics as a tool for intrusion detection. Their findings could inspire further research and inform the development of new biometric applications. In another study, which has not yet been published, the researchers also compiled their own dataset of mouse usage data and evaluated it.
"The results of these evaluations are similar to those gathered using the Balabit dataset, despite the fact that the new dataset contains data of more users," Antal said. "This result is very encouraging. We also started applying deep learning for feature extraction, exploring whether features produced using deep learning could be better than hand-crafted ones."
More information: Intrusion detection using mouse dynamics. arXiv:1810.04668v1 [cs.HC]. arxiv.org/abs/1810.04668
A new biometric technology based on mouse dynamics. ieeexplore.ieee.org/document/4288179
© 2018 Tech Xplore


















