Verifiable searchable symmetric encryption for conjunctive keyword queries in cloud storage
Searchable symmetric encryption (SSE) has been introduced to enable secure outsourcing of encrypted databases to cloud storage, while maintaining searchable features. Of the various SSE schemes, most assume the server is honest but curious, while the server may be trustless in the real world.
Considering a malicious server not honestly performing the queries, verifiable SSE (VSSE) schemes are constructed to ensure the verifiability of the search results. However, existing VSSE constructions only focus on single-keyword search or incur heavy computational cost during verification.
To address this challenge, a research team led by Joseph K. Liu published their new research on 02 April 2022 in Frontiers of Computer Science.
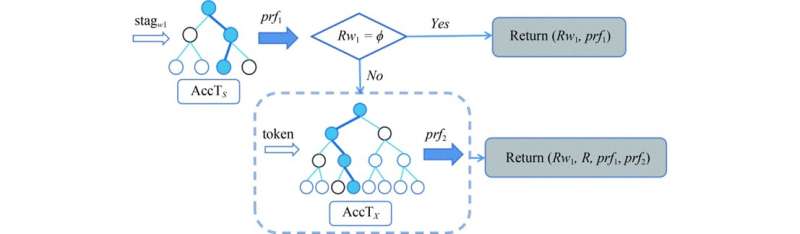
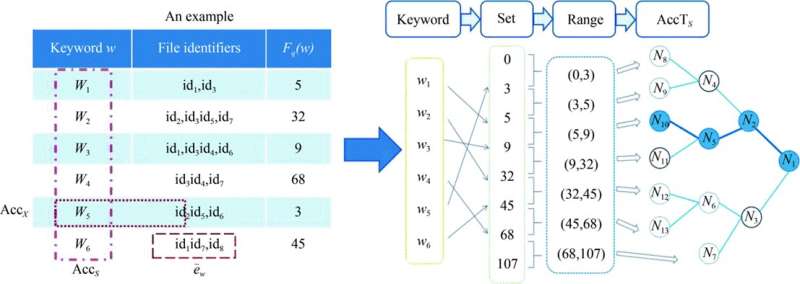
The team proposes a new VSSE construction supporting conjunctive keyword queries, which can be treated as an improvement of a recent VSSE solution. The proposed VSSE scheme is based on a privacy-preserving hash-based accumulator, leveraging a well-established cryptographic primitive, Symmetric Hidden Vector Encryption (SHVE). The VSSE scheme enables both correctness and completeness verifiability for the result without pairing operations, thus greatly reducing the computational cost in the verification process.
More information: Qingqing Gan et al, Verifiable searchable symmetric encryption for conjunctive keyword queries in cloud storage, Frontiers of Computer Science (2022). DOI: 10.1007/s11704-021-0601-8