This article has been reviewed according to Science X's editorial process and policies. Editors have highlighted the following attributes while ensuring the content's credibility:
fact-checked
trusted source
proofread
Algorithm advances uncompromising covert communication

A new algorithm that can enhance covert communication without compromising data integrity is reported in the International Journal of Autonomous and Adaptive Communications Systems.
Mingfang Jiang of the School of Computer Science at the Hunan First Normal University in Changsha, China, has introduced an innovative algorithm, RDHEIAC (Reversible Data Hiding for Encrypted Images Algorithm with Adaptive Total Variation and Cross-Cyclic Shift). The work marks a significant step forward in information security and covert communication. The algorithm addresses the limitations of traditional methods by allowing the embedding of additional data into carrier data without compromising the integrity of the original information.
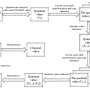
RDHEIAC departs from the conventional and employs adaptive total variation to generate a prediction error image. This optimizes the process for reduced prediction errors and improved embedding rates of secret messages. This ensures that additional data can be embedded seamlessly into the carrier data, allowing complete recovery of the original information without any damage.
Jiang's work also explains how RDHEIAC integrates various techniques such as bit-plane rearrangement, run-length encoding, cross-cyclic shift operation, diffusion operation based on chaotic maps, and bit substitution to do its job. These methods collectively contribute to the creation of secure encrypted images with a balance between privacy security, high embedding capacity, and image fidelity.
Preliminary tests demonstrate the algorithm's efficiency, showing it can achieve a notable, about 47%, increase in embedding rate compared to previous RDHEI-type algorithms. The main application, of course, is covert military and business communications, but the same technology could be useful in medical imaging where privacy is paramount but there is a vital need for image integrity.
One notable feature of the RDHEIAC approach to image encryption and message embedding is that it keeps the information extraction and image restoration separate. This provides flexibility in scenarios demanding high information integrity. An additional possibility with this approach is being able to adding reversible visible watermarking in encrypted images.
More information: Mingfang Jiang, Reversible data hiding algorithm in encrypted images using adaptive total variation and cross-cyclic shift, International Journal of Autonomous and Adaptive Communications Systems (2023). DOI: 10.1504/IJAACS.2023.134851