This article has been reviewed according to Science X's editorial process and policies. Editors have highlighted the following attributes while ensuring the content's credibility:
fact-checked
trusted source
proofread
Between one and all: Researchers propose system to control selected devices on network
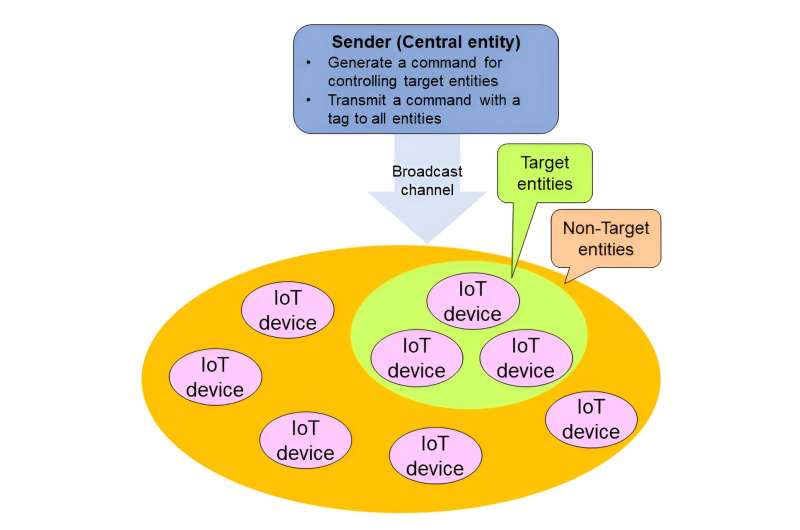
One or all—that's the current choice many networks give users when it comes to controlling smart devices. With the evolving Internet of Things (IoT), referring to the technology that connects devices to one another and to the cloud, users need more specific control over their devices. Now, a Japanese team of researchers has developed a solution that may allow both more efficient and more secure control.
The United Nations' International Telecommunication Union has published the proposed broadcast authentication system as an ITU-T Technical Report "TR.ba-iot."
"In the future, a wide variety of many IoT devices will be connected to the network," said Junji Shikata, who is a professor on the Faculty of Environment and Information Sciences, and at the Institute of Advanced Sciences at Yokohama National University in Japan. "Our research team has proposed a broadcast authentication system in which a sender has the ability to control a number of arbitrary target devices remotely and simultaneously."
Imagine a smart home, with lights, a security system, entertainment devices and a thermostat, all controlled from a contracted service provider. The smart home service provider can monitor lifetime and abnormal communication of each IoT device and send commands to the devices one at a time. It's possible for the owner and smart home service provider to automate the process but the device-to-device communication remains the same.
"When unauthorized communication, such as a cyberattack, is detected in a wide variety of IoT devices installed in a smart factory, administrators can control the IoT devices and prevent the spread of damage," Shikata said. "In addition, this system could be also applied to services such as remotely shutting down IoT devices installed at dams, underground facilities and more that are difficult for people to access when the device reaches the end of its lifecycle."
The broadcast authentication system proposed by Shikata acts as a simplified remote control. The sender can broadcast a control command to all IoT devices in the network but limit it so that only designated devices may execute the command. Every device receives and assess the command, but only target devices will follow the direction.
"The broadcast authentication system makes it possible to efficiently control arbitrary multiple IoT devices simultaneously with a broadcast communication for IoT devices connected to the network," Shikata said. "For example, it can be applied to the control of IoT devices infected with malware or IoT devices that are left in the network beyond their lifespan, in order to turn them off and isolate them from the network."
Crucially, Shikata said, the conceptual model clarifies the security characteristics and requirements required for a broadcast authentication scheme. This includes using a message authentication code and a digital signature, both of which help ensure the integrity of the data shared was not compromised in transit.
Next, Shikata said he plans to continue developing practical and secure next-generation cryptographic technology.
More information: Broadcast authentication scheme for Internet of things (IoT) system (2023)