Japan's 'flying car' gets off ground, with a person aboard (Video)
The decades-old dream of zipping around in the sky as simply as driving on highways may be becoming less illusory.
Aug 28, 2020
23
78013
Hi Tech & Innovation

The decades-old dream of zipping around in the sky as simply as driving on highways may be becoming less illusory.
Aug 28, 2020
23
78013
Internet

We've all done it. We're updating the operating system on our mobile phone or installing an app, and we lazily skim through the privacy policy or we don't bother to read it at all before blindly clicking "I agree."
Jan 29, 2020
0
2
Energy & Green Tech

The saying that "misfortune never comes alone" is also the title of a French short silent film from 1903. One could say the same about the climate crisis, which is closely linked to the environmental and energy crises. The ...
Apr 11, 2023
7
1369
Internet

Aquatic internet that sends data through light beams could enable divers to instantly transmit footage from under the sea to the surface.
Jun 11, 2020
0
34188
Internet

Tim Hart was sitting on his couch one evening in November 2011 when he got an email with the subject line: "I'm watching." The message that followed was short and to the point …
Feb 26, 2021
0
10
Business

A gray-haired man walks through an office lobby holding a coffee cup, staring ahead as he passes the entryway.
Mar 3, 2023
0
250
Computer Sciences

Two researchers at Emercoin, a decentralized peer-to-peer (p2p) network providing secure blockchain business services, have recently developed a new technology called Randpay that only allows users to complete payments and ...
Business

California will be the first state to require online companies to put kids' safety first by barring them from profiling children or using personal information in ways that could harm children physically or mentally, Gov. ...
Sep 16, 2022
0
59
Security
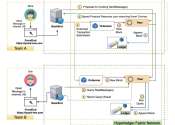
Data and security breaches are becoming increasingly common, highlighting the vulnerabilities of existing messaging and communications platforms. Devising computational tools and systems that better protect sensitive data ...
Engineering

Honda has announced on its News Room website the establishment of a startup called Ashirase, Inc.— the first new business venture to originate from the company's IGNITION program. Ashirase will produce an in-shoe navigation ...