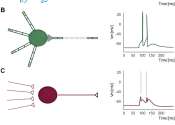
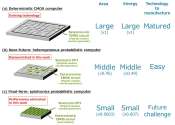
Holographic displays offer a glimpse into an immersive future
Setting the stage for a new era of immersive displays, researchers are one step closer to mixing the real and virtual worlds in an ordinary pair of eyeglasses using high-definition 3D holographic images, according to a study ...
Apr 23, 2024
0
53