This article has been reviewed according to Science X's editorial process and policies. Editors have highlighted the following attributes while ensuring the content's credibility:
fact-checked
trusted source
proofread
OneButtonPIN increases security for blind and low-vision tech users
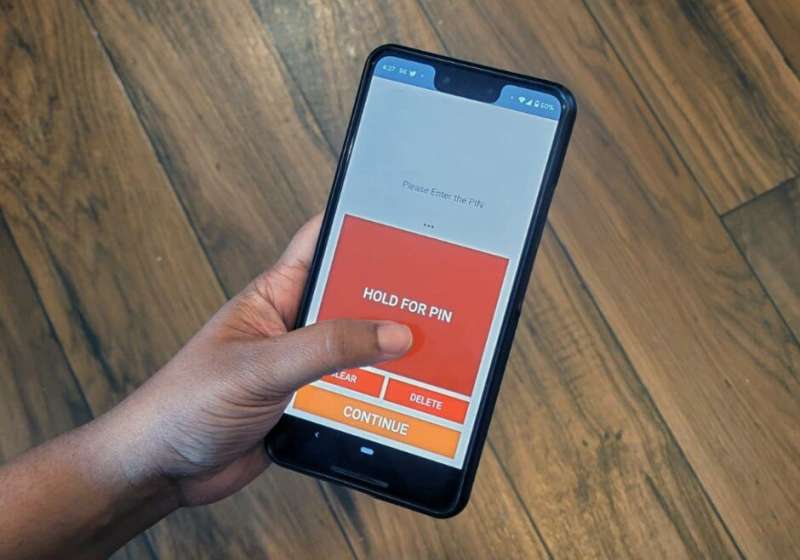
Working closely with blind and low-vision (BLV) users, researchers at the University of Waterloo and the Rochester Institute of Technology have developed a new authentication method that could help BLV technology users more securely access their devices. The new method, OneButtonPIN, allows users to input PIN codes using a single large button and a series of haptic vibrations.
People with BLV frequently express frustrations with existing authentication methods such as drawing patterns, fingerprint and face scans, and PIN codes. Some methods are difficult to use effectively without visual data. Others are vulnerable to privacy attacks.
OneButtonPIN addresses these security issues by using haptic vibrations imperceptible to outsiders. When prompted to enter a PIN code, the user presses and holds a large button on their smartphone screen. This activates a series of vibrations separated by pauses; the user counts the number of vibrations corresponding to the number they desire to enter, then releases the button and repeats the process until the desired numbers are entered.
While biometrics such as fingerprints and face scans are unique and easy to use, a person's biometrics cannot be changed or reset, explains Stacey Watson, a lecturer in computer science and one of the researchers on the study.
"More traditional forms of entry are vulnerable due to many BLV people's use of screen reader technology," said Watson. "PIN users are vulnerable both to eavesdropping and shoulder surfing attacks, which is where someone nearby can observe a user's device without their knowledge."
In a research study, nine BLV participants installed OneButtonPIN apps on their phones. They were first tasked with entering randomly generated PINs using the OneButtonPIN method several times, then instructed to use the app at least once a day for a week as part of a diary study. The study revealed that OneButtonPIN allowed users to input codes with an average of 83.6 percent accuracy or above, as opposed to 78.1 percent accuracy using traditional methods.
The method also proved to be incredibly secure. In the second stage of the study, 10 sighted participants watched videos of people using both traditional PIN entry methods and OneButtonPIN, then attempted to guess their PIN codes. Every participant was able to successfully guess users' PINs using traditional methods, but no one could successfully guess code input using OneButtonPIN.
"While OneButtonPIN was designed for BLV people, many users will appreciate the added security," Watson said. "When we make things more accessible, we make things more usable for the average user as well."
The study was published in the Proceedings of the ACM on Human-Computer Interaction.
More information: Manisha Varma Kamarushi et al, OneButtonPIN: A Single Button Authentication Method for Blind or Low Vision Users to Improve Accessibility and Prevent Eavesdropping, Proceedings of the ACM on Human-Computer Interaction (2022). DOI: 10.1145/3546747