This article has been reviewed according to Science X's editorial process and policies. Editors have highlighted the following attributes while ensuring the content's credibility:
fact-checked
proofread
Linkable and traceable anonymous authentication with fine-grained access control
Anonymous authentication plays a crucial role in privacy-focused applications, and it is used for authenticating a user's identity in a privacy-preserving way. If enough privacy is provided, malicious users may misuse privacy. Accountability is necessary to avoid abusing anonymity. Previous anonymous authentication schemes can not hold the basic requirements of public linking and tracing while further ensuring access control simultaneously.
To address the problems, a research team led by Junzuo Lai published their research in Frontiers of Computer Science.
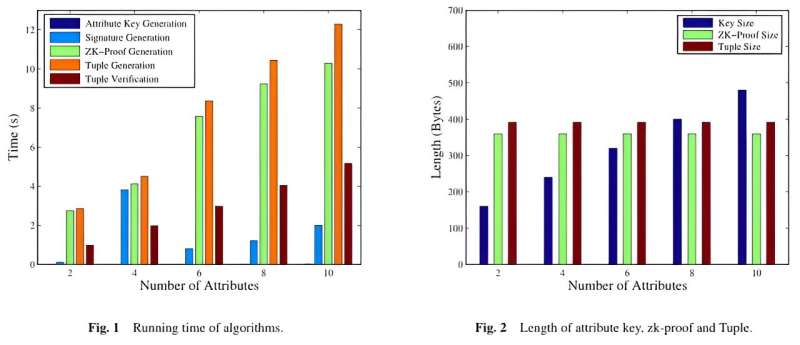
The team proposed a linkable and traceable anonymous authentication with fine-grained access control, supporting access control, anonymity, public linkability, and public traceability at the same time. The proposed scheme does not need a trusted authority to detect malicious behaviors. Anyone is able to judge whether a user authenticates multiple times or not, and further find its identity. A formal security proof and the experiment data show the efficiency and feasibility of the proposed scheme.
Future work can focus on expanding the scheme to a multi-authority scheme, allowing each authority to issue an attribute key corresponding to a certain attribute to a user.
More information: Linkable and traceable anonymous authentication with fine-grained access control, Frontiers of Computer Science (2024). DOI: 10.1007/s11704-023-3225-3