This article has been reviewed according to Science X's editorial process and policies. Editors have highlighted the following attributes while ensuring the content's credibility:
fact-checked
preprint
trusted source
proofread
Navigating digital financial inclusion in Africa
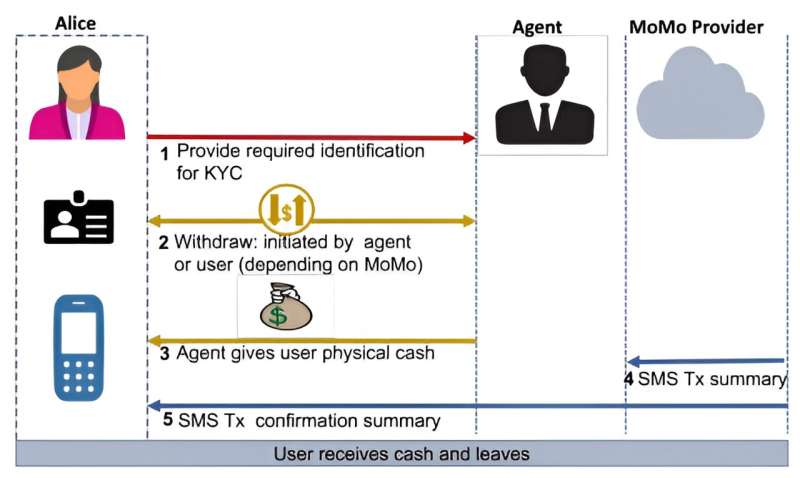
As the presence of mobile phones becomes increasingly widespread in Africa, digital services have allowed for more financial inclusion among low- and middle-income countries within the continent. Through a system known as mobile money (MoMo), users are able to make transactions through telephone companies, using their phone number as an account number as opposed to opening a traditional account at a financial institution.
Telephone companies rely on third parties known as "agents" to digitize physical cash and facilitate these transactions. However, although the convenience of this system allows a larger population base to be reached, it brings with it unique privacy and security challenges.
A group of Carnegie Mellon University researchers led by Karen Sowon, a postdoctoral researcher at CMU's CyLab Security and Privacy Institute, investigated these issues and recently published a paper titled "The Role of User-Agent Interactions on Mobile Money Practices in Kenya and Tanzania" on the arXiv preprint server.
The work, which includes researchers from CMU's Pittsburgh campus and Kigali location, was presented at the 45th Institute of Electrical and Electronics Engineers (IEEE) Symposium on Security and Privacy (SP 2024), held in San Francisco May 20–23.
The paper presents data from 72 interviews with MoMo users in Kenya and Tanzania. The researchers discovered three primary insights related to the interactions between users and agents. First, they identified and categorized the many challenges users face when engaging with the MoMo system and the potential causes behind them. These included issues with know-your-customer (KYC) compliance, interface accessibility and usability, and privacy and security concerns with agents.
Subsequently, they were able to highlight the various workarounds that both users and agents utilize to circumvent these challenges and their associated risks, as well as identify reasons users would choose one agent over another.
"We found that factors like choice of agent were not just for convenience, but also because people thought it might mitigate some of the inherent privacy risks of MoMo or the ones the workarounds were creating," said Sowon. "For example, some users, when transacting large amounts of money, would use an agent in another town or place where they are completely unknown instead of the agent they would normally use to create anonymity. But, of course, there are privacy and security risks with that, too."
Following this study, Sowon and her team have a better idea of some of the considerations their future solutions must include. The difference between basic feature phones common in Africa and smartphones present the challenge of exclusivity and ensuring that the technical solutions they create are accessible to all users.
"In situations where people don't have mobile money, they could potentially be left out of economic opportunities and exacerbate their economic status," Sowon explained. "So, we need to be thinking of things like this in terms of inclusion and future solutions."
Sowon and her team are now evaluating new MoMo protocols that could address some of the challenges identified in their study, such as allowing people to authenticate themselves to the MoMo system without having to share their personal information with an agent.
More information: Karen Sowon et al, The Role of User-Agent Interactions on Mobile Money Practices in Kenya and Tanzania, arXiv (2023). DOI: 10.48550/arxiv.2309.00226